Manažment dát
Vedúci výskumu Mgr. Jana Uramová, PhD. , , doc. Ing. Jozef Papán, PhD.
Network data are an integral part of cyber security solutions. In our research we are dealing with:
- Collecting, archiving and processing network data that can be used for forensic analysis and creating datasets,
- Creating comprehensive and reliable datasets that are needed in the process of training and testing of all new methods for detecting network attacks and anomalies.
- Effective monitoring, data analysis and visualization,
- Flow control for faster routing in IP networks.
We discuss our current results; links to industry practice and future research in the following pages.
We use our experience with Moloch as a scalable, open source packet-capture tool to effectively monitor and archive network flows. We use the ability of the tool to analyze, index billions of network sessions, the ability to use a fast and easy-to-use web application to search a large set of captured packets. Browsing is possible on the basis of arbitrary parameters (IP, GeoIP, URL, file type, ..), with the possibility of subsequent forensic analysis for detecting network intrusions (malware, intrusions, scanning, …). By linking this tool with other tools, such as network intrusion detection tools (in our case IDS Suricata), analysis and other possible uses are greatly accelerated.[1]
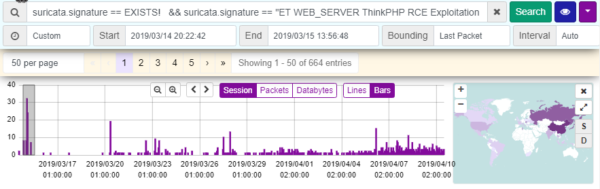
A quality data set allows us to identify the ability of a method or system to detect anomalous behavior, but also allows us to provide potential efficiency when deployed in real operating environments. Datasets play an important role in testing and validating network anomalies detection methods or systems. The solved problem is the analysis of existing known datasets containing both normal and offensive traffic, and the creation of our own datasets to meet the criteria for a comprehensive and reliable dataset. [2]
Collection of data is rarely a goal in itself. The collection is usually performed to fulfill a business requirement of an organizational unit (a company, a government institution, …). The business requirements may be diverse, for instance:
- dimensioning and management of net infrastructure,
- dimensioning and management of application infrastructure,
- defense against attacks from the Internet,
- defense against leaking of confidential data from the intranet,
- detection of net failures, attacks or anomalies.
Fulfillment of these requirements requires processing of data into a form, where a human, or a specialized software can use them in decision making process.
In the case, when a human makes a decision it is important to provide her with a summary, from which an informed intervention can be made. Such summary can take the form of a graph, diagram, or a table. Such visualizations can be prepared beforehand for known problems for which relevant statistics are known. But there may be novel problems, and for this reason it is important to have a flexible infrastructure for visualization. In our team, we develop visualizations of data sets in R statistics software.
If the method implemented in hardware or software is decisive, the current research problem is pre-processing of captured data, identification and selection of important features from the IP network flow, that are sufficient to describe the stream, and which the new proposed methods for detection of anomalies in network flow (based on machine learning), used for training or testing, and can be used in real time.
One of the decision mechanisms implemented in the software on routers is a routing protocol. One of its required features is a fast response to an unexpected node or link failure primarily in the ISP network and successive repair.
After a link or node failure, the network convergence process of the Interior Gateway Protocol (IGP) may take hundreds of milliseconds or more. Because this time is insufficient for current ISP business requirements, Fast ReRoute (FRR) mechanisms have been developed to reduce network convergence time and minimize transmission loss. FRR mechanisms are usually based on a proactive approach – a pre-calculated alternative path before a failure occurs. When a failure is detected, the router running FRR will immediately use this backup path in response to the failure, instead of calculating the replacement path after the failure occurred. Our research team has developed a new innovative FR-M-REP mechanism. [3][4][5][6][7][8].
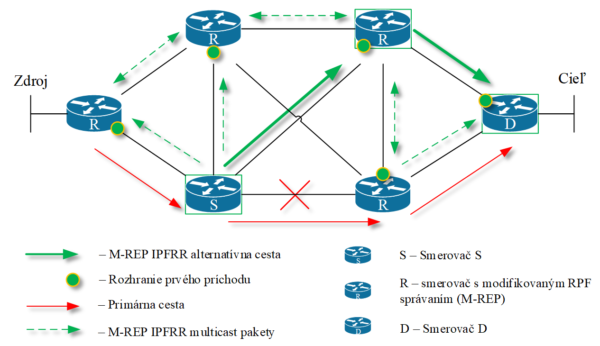
The main benefit of FRR technology is guarantee of data availability and fast connection recovery. This technology is designed for clients and ISPs who require continuous connectivity with minimal times of distruption.
References
[1] J. Uramova, P. Segec, M. Moravcik, J. Papan, T. Mokos, and M. Brodec, “Packet capture infrastructure based on Moloch,” in 2017 15th International Conference on Emerging eLearning Technologies and Applications (ICETA), 2017, pp. 1–7.
[2] J. Uramova, P. Scgec, M. Moravcik, J. Papan, M. Kontsek, and J. Hrabovsky, “Infrastructure for Generating New IDS Dataset,” in 2018 16th International Conference on Emerging eLearning Technologies and Applications (ICETA), 2018, pp. 603–610.
[3] J. Papan, P. Segec, P. Paluch, J. Uramova, and M. Moravcik, “The new Multicast Repair (M-REP) IP fast reroute mechanism,” Concurr. Comput., 2018.
[4] J. Papan, P. Segeč, M. Moravčík, M. Konštek, L. Mikuš, and J. Uramova, “Overview of IP Fast Reroute Solutions,” in ICETA 2018 – 16th IEEE International Conference on Emerging eLearning Technologies and Applications, Proceedings, 2018.
[5] J. Papan, P. Segec, M. Moravcik, J. Hrabovsky, L. Mikus, and J. Uramova, “Existing mechanisms of IP fast reroute,” in ICETA 2017 – 15th IEEE International Conference on Emerging eLearning Technologies and Applications, Proceedings, 2017.
[6] J. Papán, P. Segeč, M. Drozdová, L. Mikuš, M. Moravčik, and J. Hrabovský, “The IPFRR mechanism inspired by BIER algorithm,” in ICETA 2016 – 14th IEEE International Conference on Emerging eLearning Technologies and Applications, Proceedings, 2016.
[7] J. Papán, P. Segeč, and P. Palúch, “Analysis of existing IP Fast Reroute mechanisms,” in International Conference on Information and Digital Technologies, IDT 2015, 2015.
[8] J. Papan, P. Segec, and P. Paluch, “Utilization of PIM-DM in IP fast reroute,” in ICETA 2014 – 12th IEEE International Conference on Emerging eLearning Technologies and Applications, Proceedings, 2015.